- About Us
- Services
- Technology Leadership
- Technology Management
- Security Management
- Technology Innovation
-
Cyber Escape Rooms
A fun-filled and scientifically-designed solution to cyber training and team building
- Resources
- Podcasts
A fun-filled and scientifically-designed solution to cyber training and team building
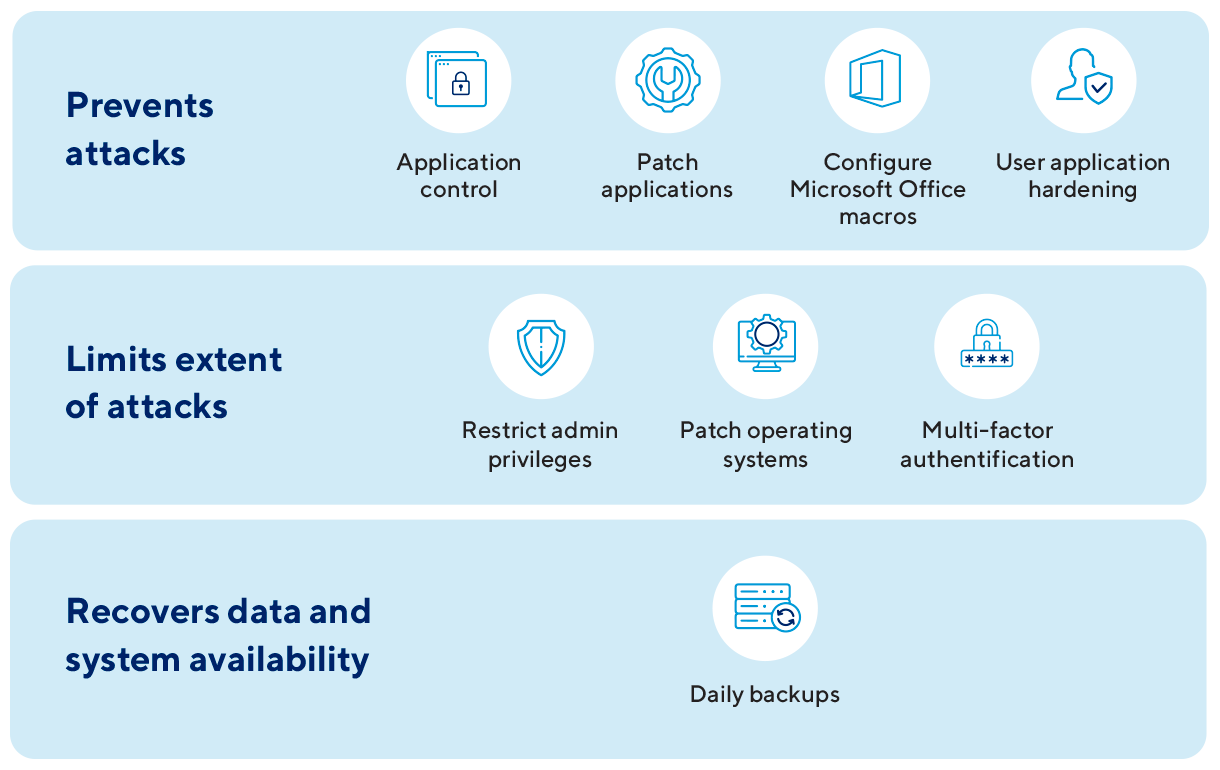
Effective cybersecurity isn’t just about tools; it’s about alignment. As organisations grow and their IT landscapes become increasingly complex, aligning to security frameworks like the Essential 8 becomes imperative. The Essential Eight consists of eight essential strategies that, when implemented effectively, provide strong protection against a wide range of cyber threats. These strategies are designed to mitigate common attack vectors and enhance an organisation’s overall cybersecurity posture.
Wyntec’s Essential 8 Alignment service ensures your business fulfils all Essential 8 requirements, encompassing assessment, implementation, and the highlighting of key solutions tailored for your needs. With Wyntec, you’re not just getting a service; you’re adopting a proactive approach to cyber threats.
Wyntec’s experts start by assessing your current cybersecurity posture to identify gaps and vulnerabilities.
We then determine which of the Essential Eight strategies are most relevant to your organisation’s needs and risks.
We implement the selected strategies with careful planning and consideration of your organisation’s requirements.
We continuously monitor your cybersecurity controls, update them as needed, and respond to emerging threats.
Take the proactive step with Wyntec and request a complimentary consultation with our expert advisors today!
Level 11, 490 Upper Edward Street, Spring Hill QLD 4000
8:30AM to 5:00PM
1300 655 523